VoIP phones, like any device connected to the Internet, can be targeted by hackers involved in fraud, theft, and other crimes. Many of these hackers hail from sophisticated operations that intend to hijack business phones for illicit calls. In 2017, telecom fraud amounted to $29.2 billion in losses, with PBX and toll fraud at the top of the list. While it’s tempting to think this number, a 25% decrease from 2015, signals a decline in phone-centric fraud, it’s more indicative of consumers’ growing shrewdness around phone scams and cybersecurity.
For a small business, losing thousands of dollars to hackers can severely damage the bottom line. Thankfully, you can greatly reduce the possibility of VoIP fraud incidents with a few simple precautions. Secure key settings on your phones, router, and business phone system to prevent intrusions that siphon money, time, and manpower.
VoIP Security Issues: Why It Matters
Credit card fraud reimbursement is protected under law, but VoIP fraud is not. The Federal Communications Commission (FCC) has yet to release regulations for VoIP fraud, which means that the customer is still held financially liable for hacked calls. Some carriers are forgiving, but as the New York Times reports, some have sued their customers in court to recoup costs in excess of $200,000 per business. Small businesses from Los Angeles to Milwaukee to Canada have struggled with major telecom corporations that insert fine print, making the end user responsible for the phone system’s security. Fortunately for VoIP users, it’s very simple to safeguard your system.
1. Secure VoIP Phones: Protect Your Credentials With Strong Passwords
According to the Internet security firm TeleSign, 40 percent of Internet users have had an account hacked, a password stolen, or notification that their credentials were compromised. In just the first month of 2019, 2.2 billion stolen emails and passwords were released online. With business phones, sometimes all it takes to hack your device is a Google search.
“The average cost of a data breach is in the millions and malicious attacks are on the rise, yet a whopping 73 percent of businesses are not ready to respond to a cyber attack.”—The Best VPN
Many VoIP devices and interfaces come with pre-set passwords that are publicly available online. Most phone web interfaces don’t have automatic lockouts, so attackers can bombard your interface with an unlimited number of keygen passwords. However, a little vigilance can keep your passwords protected.
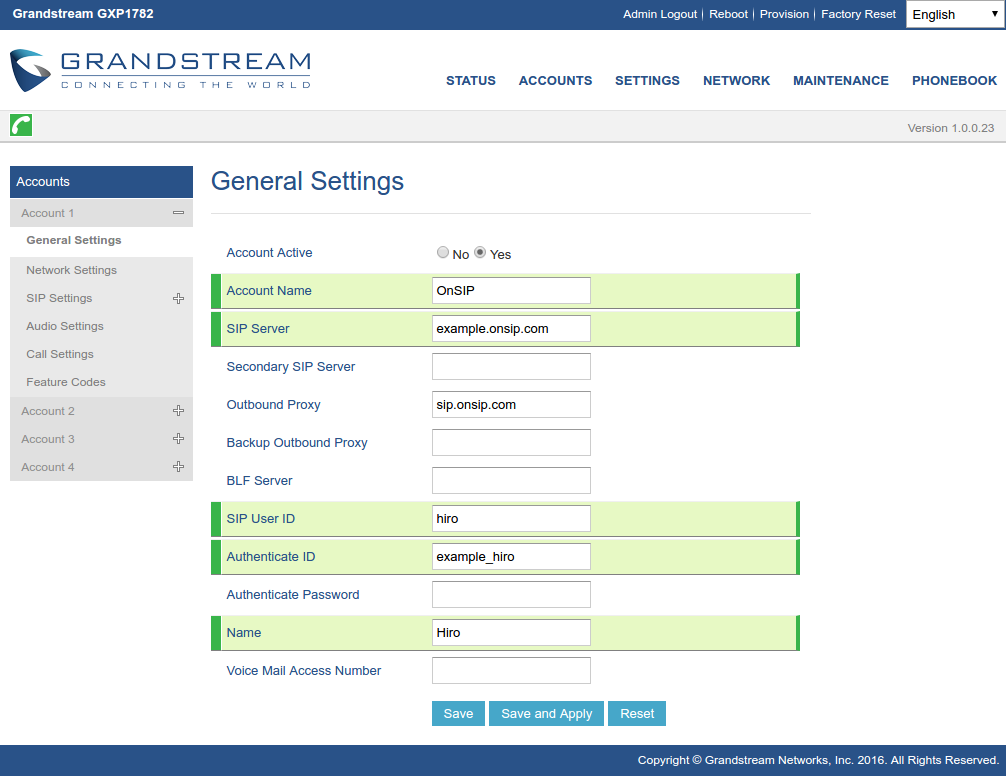
When you buy a new business phone or need to reset a phone to factory defaults, the first thing you should do is change the password. Say it with us: Change. Your. Password. Chances are, if you don't reset the password right away, the initiative will slip from your mind. Some phones use the same password across both the phone interface and the web interface. Others have separate passwords. If they are separate, don’t use the same password for both!
.jpg)
You should change your passwords every six months to a year, according to password security expert and author of Perfect Passwords Mark Burnett. According to How To Geek, a strong password:
- Has 12 characters, minimum
- Includes numbers, symbols, capital letters, and lowercase letters
- Isn’t a dictionary word or combination of dictionary words
- Doesn’t rely on obvious substitutions (e.g., h0use for house)
Don't forget to update the admin portal password for your VoIP service provider as well. If hackers find a way into that, the results could be just as damaging. Besides desk phone passwords, also remember to update any softphone/webphone accounts if you have them.
Your own phones aside, make sure that your users have secure devices. After all, you're on the same phone bill. Finally, don't share your SIP credentials with anyone.
2. Enable Network Address Translation (NAT)
NAT is a router feature that provides your VoIP phones, computers, and other devices with a private IP address that can only be seen on your Local Area Network (LAN). This IP masking acts as a barrier between the phone and traffic from the open Internet. If a hacker can't discover the private IP address of your device, then he can't manipulate the device remotely.
VoIP phones that don't use NAT are much more vulnerable to attacks. Hackers often use automated programs to scan for endpoints that are not behind NATs. A VoIP phone with a public IP address might get inundated with "ghost calls," or calls that ring your phone just to see what your device is. This is a reconnaissance technique used by hackers to feel out a target.
That's why having a private IP address is so important. NAT is another layer of protection between your VoIP phone and any individuals who may be trying to exploit it. For more information on NAT and the routers that have the feature, consider some of our previous blogs on the topic:
- What Are NAT and Firewall Traversals?
- What Is NAT Keepalive?
- Best Business VoIP Routers: The Features and Prices You Need
3. Disable Phone Web Interface
Your VoIP phone's web interface allows you to set and update many key phone properties, including the business VoIP accounts registered to the phone, network and SIP settings, codecs, call settings, and other fundamental features. The web interface also allows you to download a backup configuration of the phone, which will reveal the usernames and passwords of the phone's users in plain text.
Your business phone's web interface is probably its most vulnerable point of entry. It is a helpful tool when used in the proper context, but is a prime target for hackers who want to manipulate your business phone for fraudulent purposes.
Hackers don't have to be on the phone's LAN to access a phone's web interface. They can do it remotely from the open Internet. All they need is the phone's private IP address.
The password protection for a phone's web interface is not necessarily secure. Many VoIP phones come with pre-set passwords that are never reset by their owners. But even if the password was changed, the hacker can discover the credentials using key cracking software.
Unfortunately, many web interfaces for IP phones don’t lock users out after numerous failed password attempts. A hacker can try ten passwords per second with key cracking software. Once a hacker successfully enters the web interface, she can change the settings on your phone and access any backup configurations.
That's why we highly recommend turning off your phone's web interface altogether. You can always re-enable the web interface later on if you need to change certain settings, although you can change most settings from the phone itself. Disabling the web interface is a different process for each phone manufacturer. Consult your phone's documentation or talk to support staff for detailed instructions.
4. Close Port 80 With a Firewall
On a router, a port is essentially an active channel to the internet. VoIP phones on a LAN need to connect to ports in order to access the internet.
.jpg)
Ports on a router are numbered between 0 to 65535. Ports 0 to 1024 are reserved for use by specific services. For instance, Internet traffic such as File Transfer Protocol (Port 20), Secure Shell (Port 22), and Hypertext Transfer Protocol (Port 80) only travels through the ports that have been specified for each protocol.
Port 80 is particularly susceptible to hackers because the traffic is HTTP, the kind you encounter on most websites. The web interface for your VoIP phone is also in HTTP, which means that hackers can potentially burrow into Port 80 on your router and access the web interface as if it were any other public website. Until you close Port 80, your phone's web interface will have a public IP address that anyone on the Internet can access.
“A vast majority of VoIP fraud cases are highly preventable," says OnSIP CEO Mike Oeth. "The cases we see often involve an active web interface or an open port 80. We recommend closing both channels to minimize the chance of VoIP fraud.”
5. Disable International Calling
Many hackers want to use business VoIP phones for fraudulent hacking operations. These operations typically try to rack up calling minutes for expensive international numbers. If you don't need to make international calls for your daily operations, it makes sense to completely disable international calling.
If you need to make calls to another country, you can purchase a calling card as a workaround. But if international calling absolutely has to be turned on, make sure to regularly monitor your phone records.
.jpg)
VoIP Fraud: 15 Minutes vs. $15,000
Scammers who want to exploit your cloud phone system will often strike during long weekends, holidays, off business hours, and other times when your office will have fewer people around. The hackers want to run up your phone bill as much as possible without you or your service provider noticing.
If you don’t already do so, start monitoring your phone activity during these off hours, or set up an automated alert system to notify you of spikes in phone usage. Implementing the five cloud security measures in this blog will greatly reduce the possibility of someone hacking into your VoIP service.
If you suspect that you've been the victim of hacking, immediately disable the compromised devices. Generate a call detail record (CDR) report to find out exactly how many unauthorized calls were made using your phone system. Then call your service provider's support staff to report the incident and secure your devices.