The wide world of VoIP has enough strange terms and acronyms that we often wonder if there ought to be an officially published Jargon-to-English dictionary. And like many terms in that dictionary, OAuth falls under the “You Definitely Know What This Is, You Just Didn’t Know Its Name” Category.
In short, OAuth is that neat little tool that lets you sign in to third-party websites via existing account logins, such as Google or Facebook. You grant the third-party website access to your information stored on those accounts without handing over your password.
OAuth Authentication
OAuth started in the mid-2000s when the social bookmarking website Ma.gnolia needed to authenticate widget access, and Twitter was working on its OpenID. One happy collaboration later, OAuth was both born and widely supported among the IETF (Internet Engineering Task Force, aka the folks who decide which bits of the Internet are official protocol). OAuth 1.0 dropped in 2010.
Authorize, not Authenticate
OAuth uses other site logins to authorize data sharing. It does not authenticate, i.e., prove that you are actually the person behind the credentials. Rather, by using external logins, OAuth provides an authentication token to the new website, allowing it to use your data as you authorized without granting full access to your account.
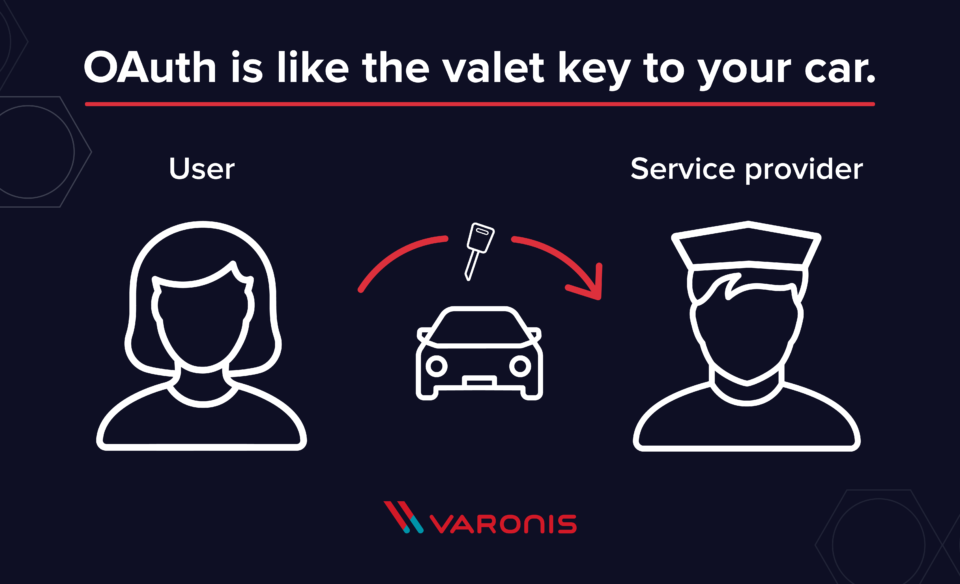
A common analogy found around the Web is the valet key. You pass off the key to the valet, authorizing him to move and park your car but not access locked areas like the trunk or glove box.
OAuth Examples
Google OAuth
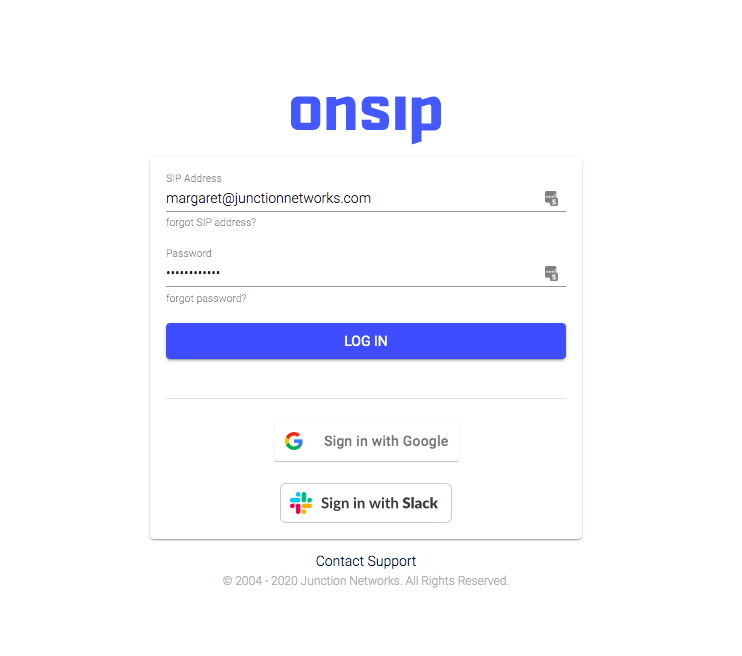
One of the most common OAuth options is to sign in with an existing Google account. This is particularly helpful for work emails that don’t end in @gmail.com but are Gmail accounts.
Slack OAuth
Another common OAuth option, again partial to work accounts, is Slack. This makes perfect sense as an OAuth login for other work accounts like your VoIP login or Twitter tools since only current employees should have Slack credentials.
OAuth 2.0
Published in 2012, OAuth 2.0 is so different from 1.0 that they’re not compatible with each other. With the goal of increasing interoperability among websites, 2.0 is scalable, with twice the number of flows to accommodate various app requirements.
Most notably, it intentionally does not support security features like encryption. CSO Online explains in more detail, but 2.0 expects those implementing it to use external protections like Transport Layer Security, something you should recognize as part of SSL—a vital security feature for any website.
Similar to vs. Sounds Like
These terms often come up when discussing OAuth. Some are related, and some just sound the same. Here’s your guide:
OpenID: An authentication protocol complementary to but fully distinct from OAuth, which is an authorization standard that can be used as part of an authentication protocol.
OpenID Connect (OIDC): An authentication standard layered on top of OAuth 2.0. Directly related to OAuth.
OATH: The initiative for building an open architecture to promote stronger authorization across the board. Unrelated to OAuth, which is a standard.
XACML: A standard for authorization policy that defines the language, architecture, and a processing model. Unrelated to OAuth, but OAuth can be used in conjunction with XACML.